Bitcoin is often critiqued for its lack of privacy and in the same breath criticized for being too private and therefore being a great option for criminals.
None of the two is true or false. It entirely depends on how you use bitcoin. In this article, we explore how you can improve your bitcoin privacy and why financial privacy matters in the first place.
Key Takeaways
- Avoid KYC as much as possible, buy with cash if you want full privacy
- Use a strong privacy wallet like Wasabi or Samourai
- Run your own node and use Tor
- Never re-use addresses
- Label UTXOs, use Coin Control and CoinJoin
- Use Lightning as much as possible
Why financial privacy matters
There are a few reasons why it's a complete misconception to believe that privacy is only important for criminals and that you’ve got nothing to hide.
Without privacy, you lose fungibility. Due to the transparency of the blockchain, you can trace back if a bitcoin has been used for criminal activities before, meaning state actors could contact you and try to seize them even when you did nothing criminal at all.
This is not something that's currently happening, but it could potentially happen down the line. You lose the fungibility that one bitcoin is always one bitcoin as newly mined ones would be more valuable than old coins that shifted through a lot of hands.
Not having privacy is impacting your economic decisions. If someone is constantly watching over you there are products or services that you maybe won't want to purchase any longer.
Data collection is a systemic risk. Having an actor that collects financial information through Anti Money Laundering and Know Your Customer guidelines can lead to systemic risk as no central actor is able to securely store this information.
And this is not just theoretical. In March 2020 a large-scale cyberattack targeted hundreds of organizations and breached sensitive data from the United States federal government.
Balaji Srinivasan, a well-known angel investor and entrepreneur, commented after the hack, " A hack means innocent citizens are now exposed to home invasions and violent attacks. Treasury must not collect data that it cannot secure. If a company gets hacked you can choose to take your business elsewhere. You have a choice. But this regulation forces everyone to send reams of sensitive data to a single place we now know to be wildly insecure. Insecure centralization of data is the true systemic risk".
The only way to effectively circumvent hacks of sensitive data from centralized databases is by not legislating that the information has to be collected in the first place.
How to improve your bitcoin privacy
Bitcoin has the ability to be used in very private and anonymous ways. General or casual usage of bitcoin is usually not very private, however, with a good understanding of the technology, you can take steps to increase your privacy and anonymity.
The first hurdle, of course, comes with buying bitcoin or getting your hands on some.
Buying Bitcoin
Most on-ramps (exchanges that take your dollars or euros and give you bitcoin in exchange) require KYC (Know Your Customer) information. Here you can already dig your privacy grave.
Binance, one of the world's largest cryptocurrency exchanges, contracts third-party vendors for KYC verification in order to handle the high volume of requests.
Buying from a centralized exchange or any regulated entity attaches your bitcoin addresses to your personal identity.
Why is this so problematic? Well, there are on-chain surveillance firms and companies that can track how you use your Bitcoin. Governments also have the ability to request this information, confiscate your bitcoin, or create tax laws that are not in your favor.
The only way to buy bitcoin anonymously is through cash. You can buy without KYC on sites like hodlhodl.com, localcryptos.com, and paxful.com.
Another option would be Bitcoin ATMs, although a good portion of them require KYC today. Using these methods, unfortunately, result in some downsides when it comes to user experience.
You can also use fully-decentralized exchanges like Bisq.
When using Bisq, your bank won’t have any clue that you’re purchasing BTC, they will just see a transfer to another account. This means your bank will know where you sent the money to, so the government knows too if they want to, but at least no random centralized company will know.

A number of peer-to-peer exchanges where users can buy and trade cryptocurrencies. Each with a varying degree of decentralization.
At the very least, ensure that you keep your KYC and non-KYC stacks of bitcoin completely separate in different wallets. The only alternative to buying Bitcoin with cash is to solo-mine a block, which surely was a great option in the early stages of Bitcoin, but is not practical for most today.
Securing Bitcoin
Next up is securing your bitcoin safely. For this, you will need to use hardware and/or software wallets.
Currently, the most popular and privacy-focused software (download onto your computer) wallet is Wasabi, followed by Samourai and Sparrow. A popular privacy-focused hardware wallet is the ColdCard.
When choosing your wallet you should lookout for a few powerful privacy-enhancing features.
- Built-in Tor to hide your IP address, essential if you want privacy
- Ability to connect to your own node. Running your own node gives you full control and even better privacy
- CoinJoin
- Coin control and labeling UTXOs
We'll dive more into running nodes, CoinJoin, Coin control, and UTXOs further into the guide.
When setting up your wallet, you'll be prompted to write down some words and keep them secret, usually 12 or 24 words. This is essentially a master password to give you access to the wallet's funds. Make sure to store it so that it's inaccessible to others. Remember that anyone who has access to your seed phrase has access to your bitcoin.
A famous adage in Bitcoin goes like this, "Holding your own keys is a big responsibility, there are no refunds in Bitcoin."
Using Bitcoin
Now that we've bought bitcoin and are securing it in our personal privacy-focused wallet, how can we actually send transactions without breaking our privacy?
A golden rule in bitcoin privacy is to never re-use addresses. Neither for sending nor for receiving.
Many privacy leaks result from address-reuse. Luckily almost all wallets will generate new addresses for you every time automatically want to transact. Just remember to never share one address with two different entities.
Addresses and their respective transactions are part of a transaction graph. If one of the addresses can be tied to an identity it becomes easier to figure out who the other address owners might be.
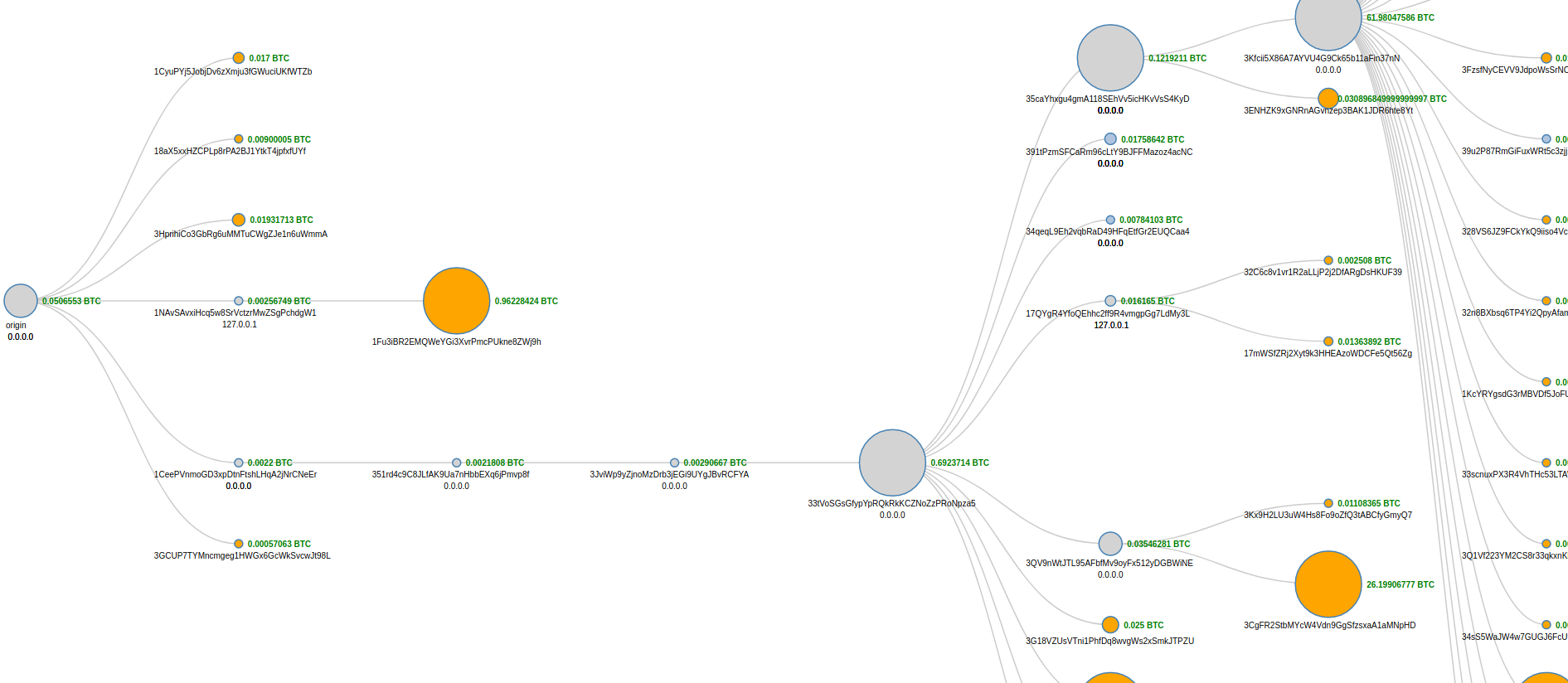
A transaction tree diagram for the wallet 1CeePVnmoGD3xpDtnFtshLHqA2jNrCNeEr and all of its corresponding transactions
Any bitcoin address is subject to network analysis, surveillance, searching the web, or a variety of other methods to identify ownership. The important practice of using a new address for every transaction is intended to make this attack more difficult.
In this context, we can use Coin control, which is the ability to selectively decide which of your coins should be used for a transaction. To understand how to use this, we quickly need to talk about UTXOs (unspent transaction outputs) to make this clear.
Bitcoin transactions have inputs and outputs. They can have one or more of each. Previous outputs can be used as inputs for later transactions. An output that hasn't been spent yet is called an unspent transaction output (UTXO).
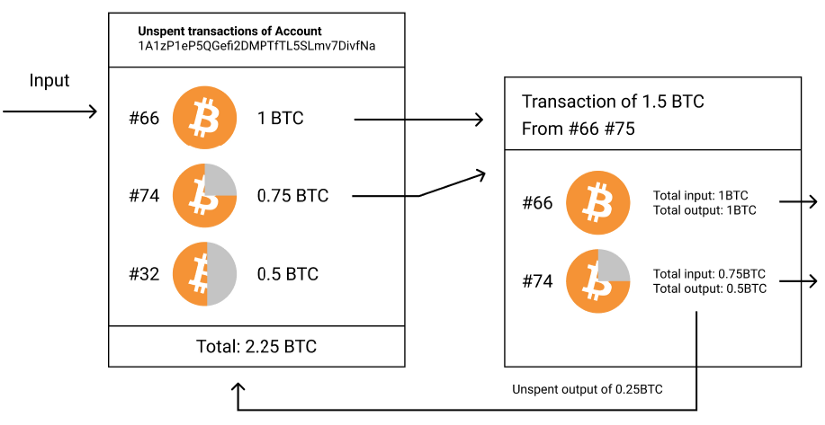
So unspent transactions are the coins that you can spend. With Coin control, you can decide which UTXOs to use to make a new transaction. Each UTXO has its own history. Coin control helps prevent address reuse and a more specific combination of addresses.
Coin control is available to use in the "advanced" settings on almost all software wallets including the accompanying software for hardware wallets Ledger and BitBox.
Running your own node
If you want full privacy you need to run your own bitcoin node. Otherwise, you are trusting a different node or server when viewing your balance, confirming incoming transactions, etc.
This node you trust might see your balances as well as sending and receiving transactions. A lightweight wallet is worse than a full node when it comes to privacy, but at least they are not as bad as custodial wallets.
Some bitcoin wallets are just front-ends that connect to a back-end server run by a company. These types of wallets have no privacy at all and the operating company has the ability to see all of the user's addresses, transactions, and sometimes the user's IP address. Users should not use web wallets.
Here is how you can set up your own node today:
- There are many options, some more technical than others. Bitcoin Core, Umbrel, RaspiBlitz are great options.
- Create a new wallet. You want a fresh wallet, that no external server has previously spied on.
- CoinJoin and send the coins from your existing wallet.
What’s Coinjoin?
Instead of sending your funds from one address to another, with CoinJoin, you join forces with many other users to create a larger transaction.
Remember that bitcoin transactions can have multiple inputs and outputs. So with a CoinJoin, what happens is that it becomes harder or even impossible to understand which of the output addresses is yours. CoinJoin is trustless (there is no third party involved as it's just a multisignature protocol, similar to how lightning channels are multisig as well).
You carry out multiple rounds of CoinJoin, one after the other, the transaction graph quickly becomes very confusing and impossible to track.
A small fee is involved to mix your coins. The fee consists of consisting of the blockchain transaction fee and the fee of the mixing pool. Samourai wallet's "Whirlpool" or Wasabi wallets integrated CoinJoin is the way to go.
Another one is Joinmarket which is really intuitive, however, not necessarily beginner friendly in my opinion.
Use the Lightning Network
Another tip for your bitcoin transactions is to use the Lightning Network as much as possible.
Bitcoin transactions are broadcast transactions, meaning everyone can take a look at them through a block explorer or by saving the chain on their node. Lightning transactions on the other hand are done off-chain between two parties. This of course improves privacy massively by default.
An Off-Chain transaction has no public addresses, no address clusters, no public transactions, no transaction amounts, or any other privacy-relevant attacks that can occur with on-chain transactions.

Usually, privacy enhancements happen by adding more data to the blockchain, which is not optimal for scaleability and also increases transaction fees (store more bytes on the chain).
Lightning does the opposite, by not storing any data on the chain at all, once payment channels are set up.
Taproot & Schnorr
On November 14th, 2021, block 709,632, Taproot was activated. It's the biggest Bitcoin upgrade in years and enables substantial privacy improvements.
Right now it's still quite visible when someone opens or closes a lightning channel. This changes with Taproot and Schnorr signatures.
Before Taproot, anyone was able to detect transactions that require the creation of multiple transactions (Lightning Network, CoinSwap, multisignature, etc).
However, the Taproot upgrade will make it possible to "cloak" all the moving parts of a Bitcoin transaction that includes these features. So even if the transactions adopt those features, they will look like a single transaction. This is a massive win for Bitcoin privacy.
Along with Taproot, Schnorr Signatures are coming to replace the Elliptic Curve Digital Signature Algorithm to enable signature aggregation.
The key advantage brought by Schnorr signatures is that they will be able to take multiple keys inside a complex BTC transaction and produce one single unique signature. This means that signatures from multiple parties involved in a transaction can be aggregated into a single Schnorr signature.
Tips and Tricks
Let's end with some final notes and tips. These are general privacy-preserving tips and are not exclusive to bitcoin.
Use encrypted text messengers like Signal and Telegram and encrypted mail like ProtonMail.
The advantages of Tor should be clear by now, and a VPN like NordVPN or ExpressVPN should be at your disposal.
Firefox browser with the uBlock Origin extension (ads and tracking blocker).
If you want to further enhance privacy, also use these add-ons: HTTPS Everywhere, Decentraleyes, ClearURLs, Cookie AutoDelete, and DuckDuckGo as your search engine. All of the mentioned extensions have Google Chrome counterparts as well.
Temporary Containers is also a great add-on isolating data across tabs, websites, and links. Bitwarden for password management. For other tweaks (and going down the privacy rabbit hole), check out https://www.privacytools.io/
To end, we'll leave you with a quote that obliterates the "I don't care about my privacy; I've got nothing to hide." argument.
"Arguing that you don't care about the right to privacy because you have nothing to hide is no different than saying you don't care about free speech because you have nothing to say." - Edward Snowden

